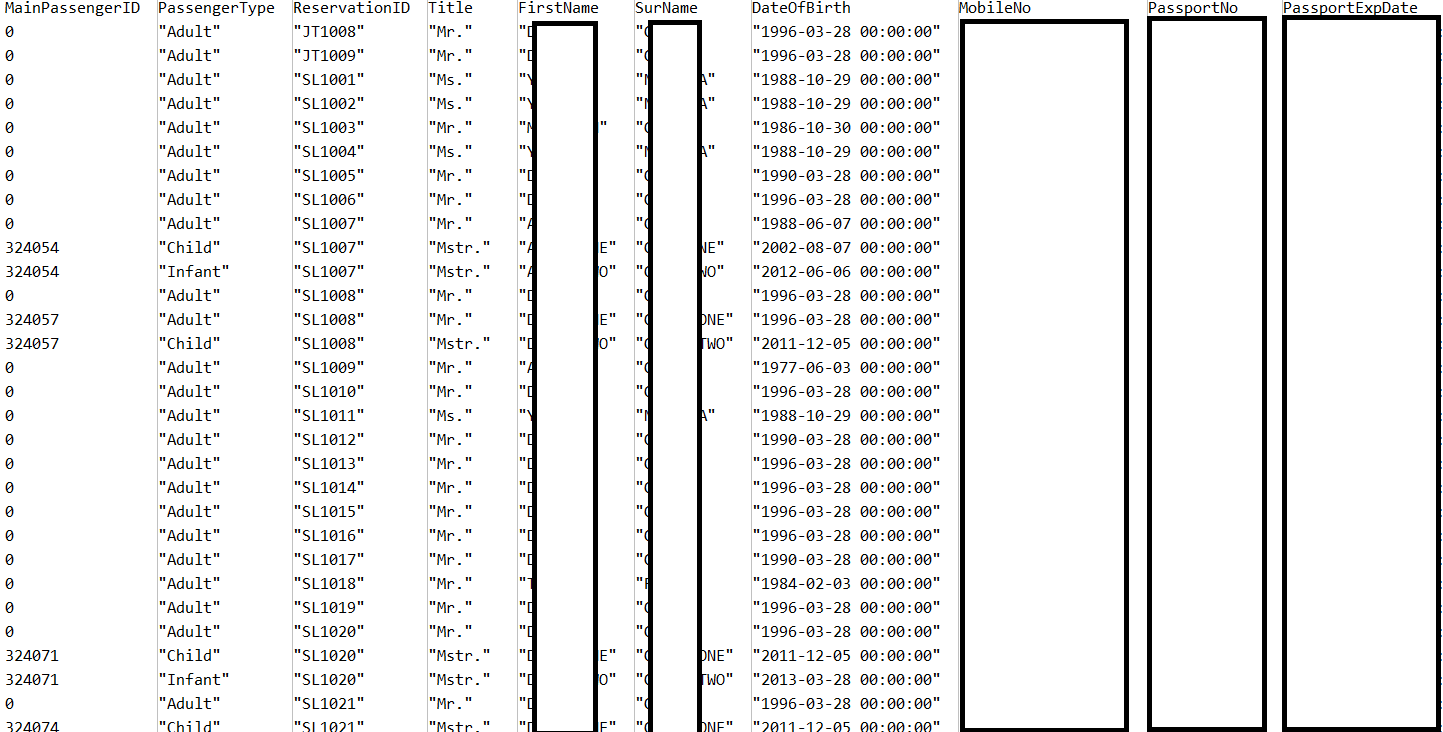
Approximately 46 million customers of Lion Air Group learned that the data they had provided to Lion Air as part of their travel regime was not only stored in an unsecured manner by Lion Air, but also availed by miscreants to the online criminal element, as evidence by the following screen shot:
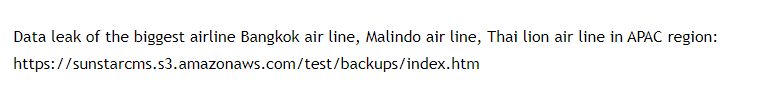
Lion Air Group includes Malindo Air, Thai Lion Air and Batik Air. According to a Malindo Air statement, the data was left unprotected by employees of their e-commerce service provider GoQuo, located in India. Two former employees were unhappy with their work and “improperly accessed and stole the personal data of our customers.”
As we’ve written before, cyber hygiene within the travel industry is lacking in far too many instances. The fact that Lion Air Group’s data was accessible to anyone who could divine the URL is disturbing. And we think there may be more to the story than Lion Air Group is sharing.
But don’t worry Lion Air Group says it’s contained! NOT!
Lion Air assures their customers that the data breach has been contained and that the matter has been reported to police in both Malaysia and India. They concluded that the breach had nothing to do with the security of the AWS (Amazon Web Services) data architecture (though the following twitter post from Under the Breach flies in the face of Lion Air assurances. They also assured their customers that credit card data was not compromised.
Actually that does not appear to be the case.
As can be seen above and below the personal identifying information of their customers was exposed, passenger names, passenger IDs, date of birth, passports data, email, phone number and reservation IDs. Enough for most any enterprising criminal to monetize via an identity theft scheme.
We urge those who have traveled on any of the aforementioned Lion Air Group airlines (Malindo Air, Thai Lion Air or Batik Air) to proactively monitor their personal identity usage in financial transactions and for those in the United States, put a credit freeze on their identities.
 Travel Securely Securely Travel
Travel Securely Securely Travel